A password should be the first line of defence for any computer or application. If a hacker can bypass a password using a password stealer, they can have free reign over the computer or app, accessing business documents, banking details, social media, email accounts and more. Any business operating today will use passwords to access these accounts. Giving account access to cyber criminals can have damaging consequences to businesses of any size. With complete control of these accounts’ cybercriminals can and will steal personal and financial information (home addresses, phone numbers, bank account details), damage a business’s reputation (hacking social media accounts, releasing or selling customer information). Password stealers are a popular way of stealing and accessing sensitive data. That’s why stopping password stealers from doing what they do is of utmost importance to you.
Note: An automatic security action is when our security tools directly deal with the malicious file by detecting, blocking or quarantining the file. SOC team interventions are when our SOC team manually quarantines the file as it has gotten past the first check from our security tools.
To illustrate the effects of this virus we’ve selected one of our customers who is subscribed to our Proactive Data Security (PDS) service. This means they will receive real-time threat protection from our SOC team. When a threat is detected we will reach out and advise on the situation. On this call our agent speaks to a small business owner who has unfortunately been infected with a trojan called Pony Stealer, a piece of malware more commonly referred to as a “password stealer”. Not only can this malware steal passwords it can also turn the device into a component of a DDoS attack, where a computer will act as a part of a wider ‘army’ of computers, designed to take down or disturb a web application. DDoS attacks and their functions are explained in more detail below.
Note: A trojan is a piece of malware that disguises or presents itself as a legitimate piece of software, hiding its malicious intentions from the user.
What is a password stealer?
A password stealer does exactly what you’re thinking it does by stealing and decrypting passwords. Pony Stealer, according to KnowBe4, is capable of stealing and decrypting passwords for over 110 different applications including VPN’s (Virtual Private Networks) FTP’s (File Transfer Protocol), emails and web browsers. All of which are common services used within business environments.
Note: : To decrypt a password is to remove any form of encryption of a password and return it to its original state (unencrypted) meaning it can be read remotely and is no longer protected. There are programmes and applications that can be used to encrypt passwords and documents; however, Pony Stealer can bypass these.
When we called the customer we let them know we had picked up a version of Pony Stealer on their device, they let us know they are usually on top of these types of things.
“I’m usually very strict when it comes to my staff keeping their passwords safe. This could have been embarrassing! Thank you.”
Unfortunately, any hard work or mindfulness concerning password best practices can be quickly undone with malware like this.
What will a password stealer do?
-
There are several ways a password stealer can end up on a device. The hacker will usually initiate the attack from one of the following:
-
Sending out mass emails, which contain prompts to download files or applications
-
Having people download and install free pieces of software online, these applications will not come from trusted sources, like Microsoft or Google
-
The hacker will gain the trust of a user as it will disguise itself as a trusted piece of software or an application that will be of benefit to them, a trojan
-
Once installed, Pony Stealer will identify the applications and services on a device that it can steal credentials from. Email applications like Outlook, web browsers such
-
Once installed, Pony Stealer will identify the applications and services on a device that it can steal credentials from. Email applications like Outlook, web browsers such Google Chrome and Microsoft Edge as well as protocols such as VPN’s (Virtual Private Network) are all vulnerable
-
When the applications are identified it will use ‘brute force’ attacks to correctly ‘guess’ the passwords of these applications. This type of attack will attempt thousands and thousands of passwords until it ‘guesses’ correctly
-
Once the computer has been completely searched, all passwords that have been ‘guessed’ will be sent back to the cybercriminals command centre
-
Once installed, Pony Stealer will identify the applications and services on a device that it can steal credentials from. Email applications like Outlook, web browsers such as Google Chrome and Microsoft Edge as well as protocols such as VPN’s (Virtual Private Network) are all vulnerable.
-
When the applications are identified it will use ‘brute force’ attacks to correctly ‘guess’ the passwords of these applications. This type of attack will attempt thousands and thousands of passwords until it ‘guesses’ correctly
-
Once the computer has been completely searched, all passwords that have been ‘guessed’ will be sent back to the cybercriminals command centre
-
The two main choices the cybercriminal has now are:
-
To steal directly from the victim
-
Or to sell the information on the dark web
-
final step that can be taken, after information is obtained, is that the hacker may use the machine to launch a DDoS attack
DDoS (Distributed Denial of Service) attacks
Once Pony Stealer is done harvesting the information from the machine it can then turn its attention to a completely different type of attack. Here’s how DDoS attacks work:
-
A DDoS attack occurs when the cybercriminal targets a website or web application with an overwhelming amount of traffic to its web server. Once the targeted website reaches its limit of traffic it will crash.
-
A cybercriminal launches a DDoS attack by recruiting thousands, sometimes millions of computers to send traffic and requests to the targeted website. This group of computers is referred to as the cybercriminal’s ‘botnet’. One computer in this ‘botnet’ is called a ‘zombie’.
-
Once a computer has become a ‘zombie’ the cybercriminal can command it to send traffic to the target. One ‘zombie’ alone will cause no damage or disruption. This is why they use a ‘botnet’ to send overwhelming amounts of traffic to the website.
-
While the computer is in its ‘zombie’ mode, all its memory and power is dedicated to the attack and not to the everyday functions the owner needs it for. Therefore, users of a ‘zombie’ computer will notice slower performance and crashing.
-
The targeted website experiences something much different. Once the websites bandwidth (the maximum amount of data an internet connection can accept of a certain space of time) is reached the performance and load times of it will become slower, impacting the end user’s usage of the website. The most successful DDoS attacks will completely take the website offline, meaning users will no longer be able to access the targeted site.
-
Often websites are targeted by rival companies to negatively impact a competing company’s reputation and drive them to their website instead. Sometimes hackers will just target a website for monetary gain, demanding a ransom in return for full functionality of the website. The main aim of an attack like this is to render a website unusable. In some cases, cyber-criminals are hired to perform attacks on rival businesses to turn their reputation to a negative one.
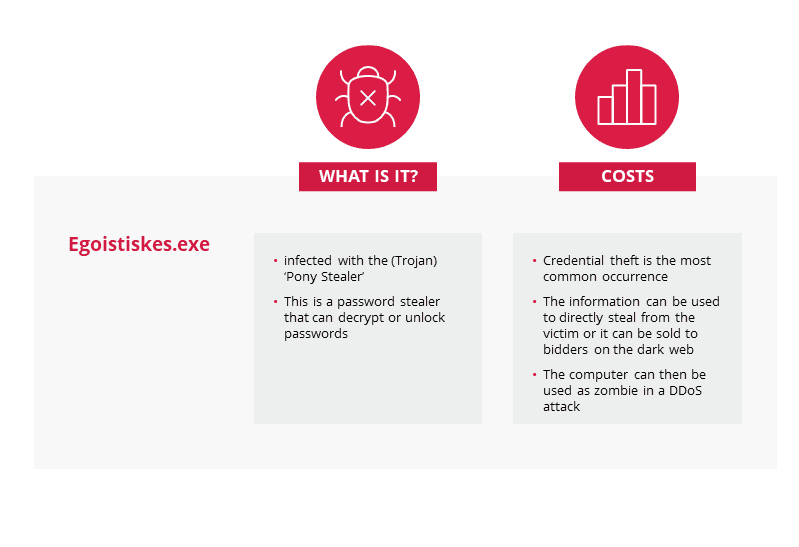
Of course, due to this merchant having installed our premium grade Endpoint Protection the file in question, Egoistiskes.exe which contained the Pony Stealer malware was quarantined the moment the download was attempted.
Note:To quarantine a file is to place it into a secure location on the device where it has no interaction with any other file or location on the host device. Our software provides its own quarantine location.
What’s the cost?
Having Endpoint Protection on this computer may have saved the business from a huge number of costs, these could have included financial and reputational losses:
-
Credential theft occurs when any information that can be used to identify a victim is stolen. This type of information can include usernames, passwords, bank account information and even home addresses. With Pony Stealer’s ability to steal passwords from over 110 different applications. Nothing is really safe. Online banking credentials, email passwords, social media logins would all be at the hands of an attacker in the case of a successful attack. This can then lead to serious financial loss and a turn to a negative reputation amongst customers if social media accounts are hacked.
-
With the use of protocols like VPNs (Virtual Private Network) and even FTPs (File Transfer Protocol) being prominent now, even in smaller businesses, Pony stealer could have assisted in the theft of any information that travels over these protocols. VPN’s will hide a user’s activity from their internet service provider; however, the service will still log and store your activity. Meaning, if a cybercriminal did gain access to your VPN they would have access to IP addresses (which can be used to track real-life location) and websites the user has visited. This information can then be sold on the dark web by the cybercriminal. The VPN being used is now just a virtual network that is being shared with a criminal. If the merchant keeps any customer databases (names, addresses, emails, recent orders), password protected or not this can be stolen. Once the attacker has this data, depending on its contents they could look to preform attacks on the customers or even just sell the information on for a profit.
-
The end goal for the attacker is to either directly steal from the victim (targeting banking information, passwords and account information) or sell on the information they obtained on the dark web. According to privacyaffairs.com, stolen online banking logins can cost as little as $40 and a hacked Gmail account can cost $80 on the dark web. This puts a frighteningly low cost on information and data that can be invaluable to merchants.
-
On the surface DDoS attacks may seem like they won’t affect the merchant, as it specifically targets a web server that has no connection to the merchant. Unfortunately, this isn’t the case. Once a merchant’s computer has been turned into a ‘zombie’ it will have drastic effects on the day-to-day operations of a business. After financial and reputational losses from the initial password stealer attack this is not what the user wants to happen. Several signs that show the merchants computer may be a ‘zombie’ include:
-
Error messages that appear seemingly from nowhere
-
Regular computer crashing
-
Loss of hard disk space
-
Closing of applications and web browsers unexpectedly
-
We took a more in depth look at what hackers can do with stolen data previously. You can read this here.
Spotting and Avoiding Trojan files
A key aspect of our calls with our customers is to ‘future proof’ them and educating business owners on the dangers of having these types of files and malware present on a computer. This is what we told the customer:
-
Our agent explained that going forward any potentially harmful files will be quarantined and explains this process. However, to completely steer clear of these files we take the steps to inform the merchant how to avoid finding these types of files in the future.
-
Our agent informed the merchant that malware like this, a trojan, will disguise itself as a legitimate application. Signs to look out for include:
-
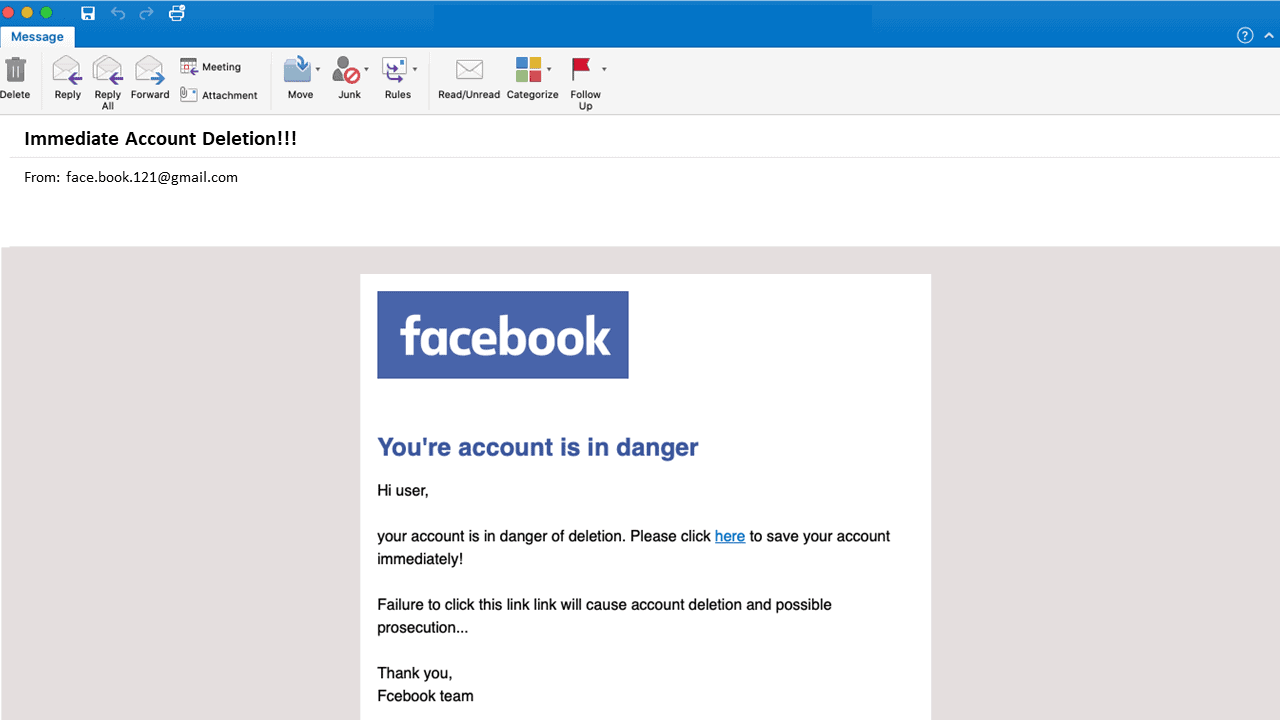
Feigning urgency – Emails containing calls to action like “Please download now for the security of your device” or “Your computer is at risk please download” should be examined carefully and deleted or passed to IT support.
-
Did the email or install come from a source that should never ask you to install an application onto your device? Companies like Google, Facebook and Amazon will never email you about downloading or installing programmes. Check emails that come from seemingly legit sources. Often fraudulent emails will be sent from email addresses that are spelled slightly wrong or they will be written in an unprofessional manner.
-
In this case the customer had downloaded a free online media player. Downloading software from unknown and untrusted sources is a major cause of viruses on computers. Often, free online programmes are open sourced, meaning the original creator allows users to change and alter the programme and more importantly, redistribute it. This way changes that are made can improve the programme. Unfortunately, cyber criminals use this type of software to input malicious code into the programme. Our agent went on to recommend installing programmes and applications from only trusted sources.
-
Implementing a strong password policy is not only adhering to PCI DSS requirements, but it also makes it more difficult for these types of attacks to succeed. For example, if your password policy requires you to have a password that is 16 characters long, containing a number, a special character, an uppercase and a lower-case letter the attacker will need to spend more time and effort guessing the password. For example a simple eight character password containing nothing but lowercase letters can be cracked instantly
|
Issue Encountered |
Action Taken by SOC |
Outcome |
|
The customer had installed a free online video player. This video player was infected with a trojan called Egoistiskes.exe which contained a password stealer called Pony Stealer. This is an application that allows cyber criminals to steal and decrypt passwords from the computer. |
The endpoint protection noticed this file may be potentially dangerous, immediately quarantined the file and sent an alert to the SOC team. The SOC team investigated the application and deemed it high risk. The customer received a phone call explaining what has happened and that the file has been placed into quarantine on the computer. |
The customer removed the file completely from the system. The SOC agent then ‘future proofed’ the merchant advising how to potentially avoid putting their computer at risk going forward. The customer’s device is now malware free. |
This piece of malware is just a small percentage of the 15,342 unique pieces of malware our security tools and SOC team have successfully identified this month. On top of this another 539 merchants have decided to opt into the excellent real time virus protection service we offer.
If you missed our last piece on the SOC team, we discussed a call we had with a merchant who had a Keygen application on their device. You can read this here.